CBC-MAC – Block Ciphers and Their Modes of Operation
14.4.3 CBC-MAC
Looking closely at Figure 14.9 again, we can see that the last cipher block c3 depends on all plaintext blocks m1,m2,m3. Of course this is also true for an arbitrary number of plaintext blocks.
Therefore, one can construct a message authentication code over some plaintext message m called the CBC-MAC by encrypting m in CBC mode, using an all-zero block as initialization vector. The CBC-MAC over m is then simply the last resulting cipher block.
While it seems attractive to have a single algorithm that can achieve both confidentiality and authenticity (we will explore this idea further in the next chapter), the CBC-MAC needs to be handled with care.
Assume Eve observes two plaintexts p1,p2 along with their corresponding CBC-MACs t1,t2. Assume further that the key ka used to compute the MACs is the same in both cases. Then Eve can construct a third plaintext p3 having the CBC-MAC t1 without knowing ka. Let p1 = m1||m2||…||mN. Then, Eve sets
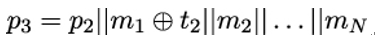
If the CBC-MAC for p3 is computed, first p2 is processed, yielding t2 as cipher block. So, for the next cipher block, (m1 ⊕t2) ⊕t2 = m1 is encrypted. So, the rest of the computation runs exactly as if p1 were processed. Therefore, p1 and p3 have the same CBC-MAC.
This issue can be avoided by using different keys for different message lengths or by prepending the message length before the actual message.
The CBC-MAC is part of the CCM mode of operation, which we will encounter in Chapter 15, Authenticated Encryption.
14.4.4 OFB mode
The Output Feedback (OFB) mode, illustrated in Figure 14.11, is a mode of operation that uses the underlying block cipher to produce blocks of keying material, which, in turn, is used to encrypt the plaintext messages. Consequently, OFB can be viewed as a stream cipher constructed from an underlying block cipher.
Informally, we can use the output blocks of a secure block cipher as keystream in a stream cipher because of Shannon’s confusion requirement we discussed at the beginning of this chapter: a cipher block should bear no traces of the statistical structure of the corresponding plaintext block. Consequently, it should have no statistical structure at all, which means it should not be distinguishable from a random block:
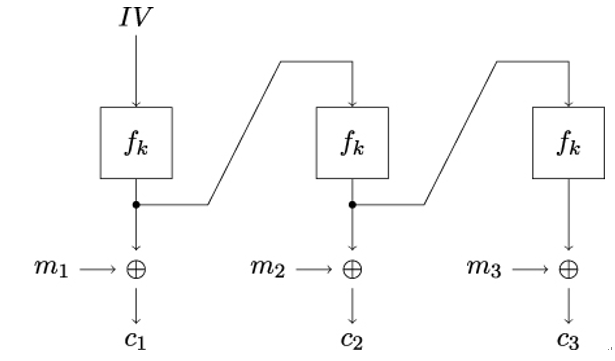
Figure 14.11: Working principle of the OFB mode of operation
To use OFB, the sender must first choose a random initialization vector IV . Using IV and a shared secret k, the encryption is done by computing:
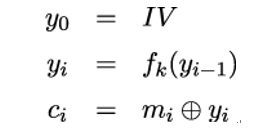
where yi is the result of encrypting input yi−1 with block cipher f under key k. All yi except y0 are used as key material that is XORed with the corresponding plaintext block mi to obtain the ciphertext block ci.
Similar to CBC, the IV is included in the ciphertext to enable decryption. The decryption is computed as follows:
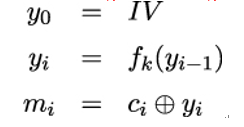
You can easily see from the above equations that, unlike CBC mode, OFB requires no inverse f−1. In practice, this is especially beneficial in resource-constrained environments such as Application-Specific Integrated Circuits (ASICs) or deeply embedded electronics because a single function can be used for both encryption and decryption. To use CBC, by contrast, designers must implement two separate functions f and its inverse f−1.
OFB has been shown to be CPA-secure if the underlying f is a pseudorandom function [117]. Moreover, unlike CBC, OFB can be used in a chained manner where the last key material block yl is used as IV for the next plaintext. In contrast, using the last ciphertext block cl as IV for the encryption of the next plaintext renders CBC vulnerable to a chosen plaintext attack. This is because Eve learns cl and, therefore, IV , which will be used to encrypt the next plaintext.
Similar to CBC, OFB encryption and decryption cannot be parallelized. However, the key material yi can be computed independently from the plaintext to be encrypted or the ciphertext to be decrypted. This, in turn, allows to pre-generate the OFB key stream, making the encryption and decryption itself very fast once the data arrives because it only involves an XOR operation.
If we want to experiment with the OFB mode, we can encrypt our plaintext in p.txt. To use AES in OFB mode, we execute the following command:
$ openssl enc -aes-128-ofb -in p.txt -out c.txt -K 000102030405060708090a0b0c0d0e0f -iv 00102030405060708090a0b0c0d0e0f0 -nopad
We can once again view the encryption result using the xxd tool. Like with CBC, the ciphertext obtained using OFB contains no repetitions:
$ xxd c.txt
00000000: 15a2 1b0d d5bd f731 0f51 ccc6 1cab f886 …….1.Q……
00000010: 59fc a0c8 7faa 1cfc dbfe e2fd 48f1 46d4 Y………..H.F.
00000020: cb7c 6e20 ef2c d2ec 8b84 ac53 51bc 9369 .|n .,…..SQ..i
We will now look at an even simpler way to use a block cipher as a key stream generator.
