CBC mode – Block Ciphers and Their Modes of Operation
14.4.2 CBC mode
Cipher Block Chaining (CBC), illustrated in Figure 14.9, is a mode of operation that chains the ciphertext blocks. CBC encryption is probabilistic, meaning that two identical plaintext blocks will result in two different ciphertext blocks:
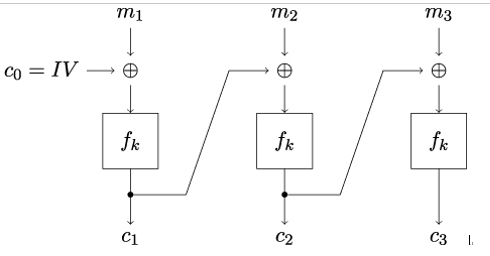
Figure 14.9: Working principle of the CBC mode of operation
The initial ciphertext block c0 is set to a randomly chosen initialization vector (IV). The following ciphertext blocks are computed by XORing the plaintext block with the previous ciphertext block and encrypting the result with the underlying block cipher:
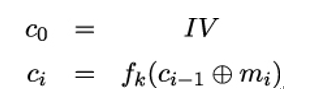
This construction ensures that identical plaintext blocks will not be mapped onto identical cipher blocks. Figure 14.10, created by Robert Graham [75], graphically illustrates this effect. As you can see, the leakage present in ECB encryption is completely eliminated:
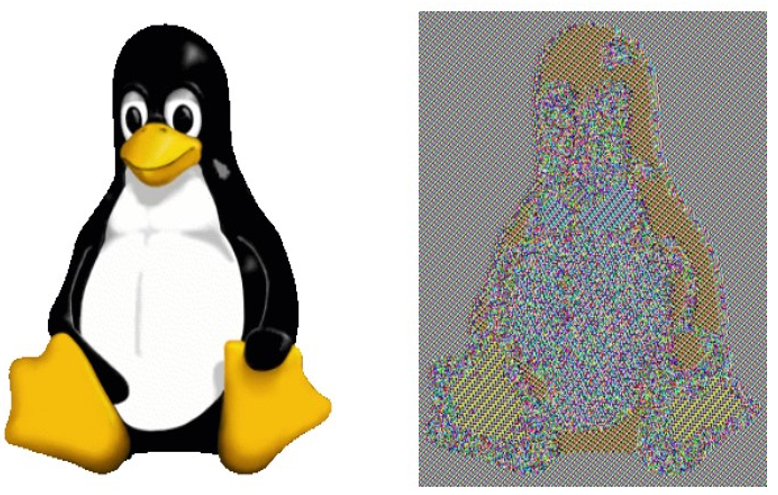
Figure 14.10: On the left, the original image of Tux, the Linux mascot. On the right, the Tux image encrypted using AES in the CBC mode of operation
Given a ciphertext c1,…,cl computed using the CBC mode of operation, the decryption is done by computing
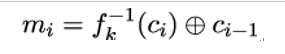
where ci and mi denote the corresponding ciphertext and plaintext blocks, and fk−1 denotes the decryption operation performed under key k. To enable decryption, the initialisation vector IV is included in the ciphertext.
Before going on to look at how we can encrypt in CBC mode in OpenSSL, we need to mention two more important properties of the CBC mode:
- A downside of CBC mode is that the encryption (and decryption) cannot be computed in parallel because the encryption of the plaintext block mi requires the ciphertext block ci−1.
- Because CBC mode uses a random IV , identical plaintexts never result in identical ciphertexts. An important consequence of this fact is that CBC encryption mode is Chosen Plaintext Attack (CPA)-secure, if we assume the underlying block cipher f to be a pseudorandom permutation. The key idea is to consider an encryption scheme CPA-secure if Eve cannot distinguish between the ciphertexts of two messages of her choice m0,m1 even if she has access to an encryption oracle. We will discuss CPA-security in detail later in Section 15.1.1 in Chapter 15, Authenticated Encryption.
To encrypt the plaintext stored in p.txt using AES in the CBC mode of operation, we need an additional 16-byte initialization vector and have to execute the following encryption command:
$ openssl enc -aes-128-cbc -in p.txt -out c.txt -K 000102030405060708090a0b0c0d0e0f -iv 00102030405060708090a0b0c0d0e0f0 -nopad$
The encryption result is again written to c.txt, and we can use the xxd tool to view the file’s contents in hexadecimal form:
$ xxd c.txt
00000000: 79a4 8518 4448 04c2 ee96 86df 5ce4 1784 y…DH……\…
00000010: 0973 6960 4b44 62dc 550c abe4 140d bc26 .si‘KDb.U……&
00000020: 2f98 c968 da10 f77b 79bc 9100 1f84 6cef /..h…{y…..l.
As you can see, although our plaintext consists of the repeating 16-byte plaintext block cryptographical1, the resulting ciphertext contains no repetitions. In real life, we would, of course, choose a completely random IV instead of 0010…f0. In addition, for every new plaintext (not a plaintext block, though) we would choose a new IV .
