General principles – Block Ciphers and Their Modes of Operation
14.2 General principles
A block cipher is an encryption function eK that maps plaintext blocks of fixed size b onto ciphertext blocks of the same size b:
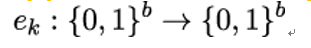
As indicated by the subscript k, a block cipher is a symmetric algorithm, taking a shared key k ∈𝒦 as a parameter, where 𝒦 is the keyspace (see also Chapter 4, Encryption and Decryption). In TLS, the shared key is agreed between client Bob and server Alice during the Handshake protocol, using public-key cryptography. Naturally, a block cipher must be a bijective function, or bijection for short (see Section 4.1 in Chapter 4, Encryption and Decryption), meaning that there is some inverse function ek−1 that reverses the action of ek and is used for decryption. Therefore, instead of writing ek−1, we will often use dk for the inverse function.
A block cipher processes the plaintext block by block, as opposed to stream ciphers, which process the plaintext bit by bit and which we met already in Section 4.5.1, Stream ciphers in Chapter 4, Encryption and Decryption. However, note that a block cipher can be turned into a keystream generator for a stream cipher; this is discussed a bit later in the present chapter in Section 14.4.
14.2.1 Advantages and disadvantages of block ciphers
Block ciphers achieve high data encryption rate, with hardware implementations being able to encrypt and decrypt at rates of several gigabytes per second. Being symmetric key algorithms, block ciphers have relatively short keys. Moreover, block ciphers can be used as primitives to construct various cryptographic mechanisms, including authenticated encryption with additional data. Finally, block ciphers have a rather extensive history and are generally well-understood cryptographic mechanisms.
On the other hand, as in all symmetric algorithms, the secret key needs to be securely distributed or established in advance (and a good practice in cryptography is to change the key frequently, ideally for each new communication session). Recall that this is also known as the key distribution problem. Moreover, the key must remain secret at all communicating parties. If Alice, Bob, and Caroline (a third party in the communication without special features) are using a single key along with a block cipher to secure their communication, it is sufficient for any one of them to lose or leak the secret key, and the security of all three of them will be compromised. On the other hand, if every possible pair of communicating parties has a unique key, then the overall number of keys to be distributed in a secure way becomes very large as it grows quadratically with the number of communicating parties.
In Chapter 7, Public-Key Cryptography, we have seen how the key distribution problem can be solved efficiently using asymmetric cryptographic algorithms. Combining these with the speedier symmetric algorithms, especially block ciphers, leads to the hybrid encryption systems we already discussed in Section 7.11, Hybrid cryptosystems in Chapter 7, Public-Key Cryptography.
