Modes of operation – Block Ciphers and Their Modes of Operation
14.4 Modes of operation
In the previous sections, we have discussed in detail how a block cipher encrypts a single block of plaintext data. But how should we proceed when faced with a large number of blocks? There are several possible answers to this question, each coming with its own advantages and disadvantages. The different approaches for encrypting a large number of blocks using a certain block cipher are called modes of operation.
As of the writing of this book, the following block cipher modes are approved by NIST:
- The modes ECB, CBC, OFB, CFB, CTR, XTS-AES, FF1, and FF3, which can be used to achieve confidentiality
- CMAC mode, which can be used to achieve authentication
- The CCM, GCM, KW, KWP, and TKW modes, which combine confidentiality and message authentication
14.4.1 ECB mode
The Electronic Code Book (ECB) mode, shown in Figure 14.6, is the most straightforward mode of operation, where the ciphertext is obtained by directly applying the block cipher to the plaintext blocks. More precisely, given a plaintext of l blocks m1,…,ml, the ciphertext is computed as
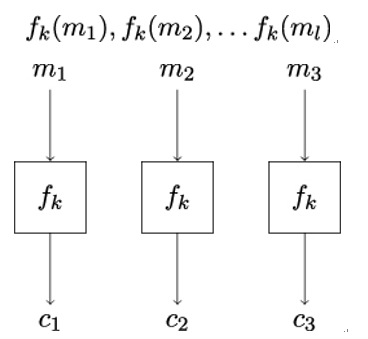
Figure 14.6: Working principle of the ECB mode of operation
From the cryptographic perspective, the ECB mode is insecure regardless of which underlying block cipher is used. This is because ECB is deterministic: any two identical plaintext blocks result in two identical ciphertext blocks. If a block repeats itself in the plaintext, the resulting ciphertext will also contain identical, repeating blocks. Moreover, if a certain plaintext block occurs more often than others, its corresponding cipher block will also occur more often in the ciphertext. More generally, the statistical properties of the plaintext on the block level leak through into the ciphertext, thereby violating Shannon’s confusion requirement.
The effect of this leakage can be seen in Figure 14.7. The original image of the Linux mascot Tux was drawn by Larry Ewing using the GIMP software; the encrypted image was created by Robert Graham [75]. Since large parts of the original image have a single color, the encrypted image is recognizable as a penguin. Note that this is despite the fact that AES encryption itself cannot be distinguished from a random permutation and, therefore, is considered secure according to the formal definition. As a result, you should never use the ECB mode of operation to directly compute the ciphertext.
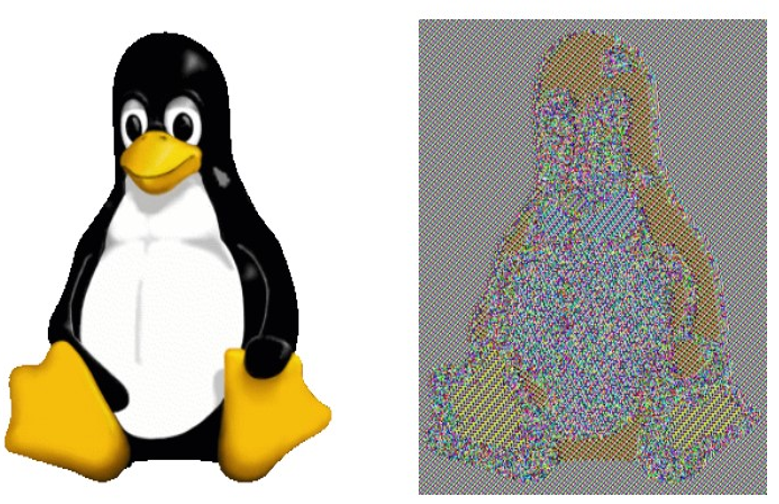
Figure 14.7: On the left, the original image of Tux, the Linux mascot. On the right, the Tux image encrypted using AES in the ECB mode of operation
On a more fundamental level, ECB illustrates an important property of cryptographic constructions: secure cryptographic primitives or building blocks can be combined or used in a way that provides no or very little security. This must be especially taken into account when dealing with large, complex security systems, mechanisms, or protocols.
Let us now do a small experiment by encrypting plaintext using the AES block cipher in the ECB mode of operation. We first need to start the OpenSSL Docker container:
$ docker container run –rm -it openssl310
In the container, we first create some plaintext and store it in the p.txt file:
$ echo -n “cryptographical1cryptographical1cryptographical1” > p.txt
With the secret key in place, we can now encrypt the plaintext stored in p.txt using AES in the ECB mode of operation and store the resulting ciphertext in the c.txt file by executing the following:
$ openssl enc -aes-128-ecb -in p.txt -out c.txt -K 000102030405060708090a0b0c0d0e0f -nopad
To see the encryption result, we have to view the c.txt file in hexadecimal form (because only a subset of values 0-255 represents printable characters). We can use the xxd tool to accomplish this:
$ xxd c.txt
00000000: aff4 ad1b b37d 74f6 7087 146e 7aa0 0414 …..}t.p..nz…
00000010: aff4 ad1b b37d 74f6 7087 146e 7aa0 0414 …..}t.p..nz…
00000020: aff4 ad1b b37d 74f6 7087 146e 7aa0 0414 …..}t.p..nz…
Every xxd output line shows 16 bytes of c.txt’s contents. As you can see, there is a repetition of the block starting with 0xaff4 and ending with 0x0414. This is not a coincidence but the result of our plaintext being composed of a 16-byte string cryptographical1 repeated three times. The ECB mode of operation turns this plaintext into a ciphertext consisting of three identical 16-byte blocks.
Filippo Valsorda, a cryptography engineer and open source maintainer, used this ECB property to generate Tux pop art shown in Figure 14.8. The different color combinations result from the use of different keys.
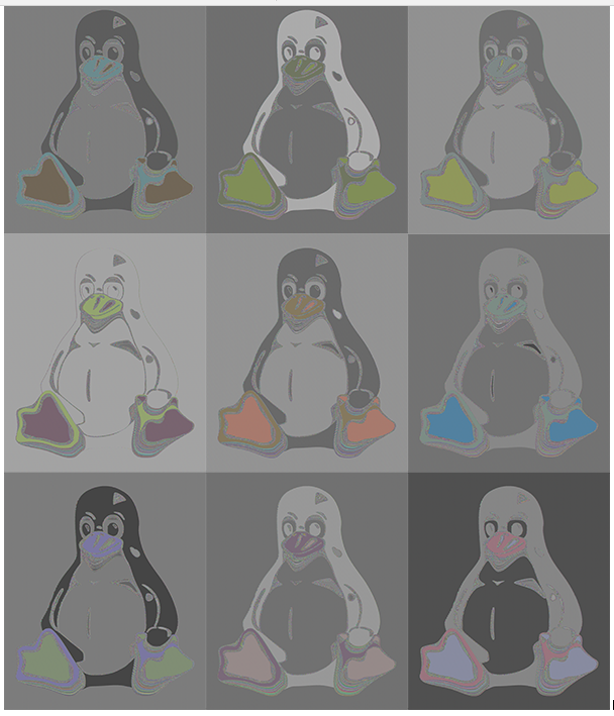
Figure 14.8: Filippo Valsorda’s Tux pop art using AES encryption in ECB mode with different keysSo, how can we fix this issue? We need to define a mode of operation that maps identical plaintext blocks onto different plaintext blocks.
