The big picture – Block Ciphers and Their Modes of Operation
14.1 The big picture
In the last part of the book, we covered in detail the TLS Handshake protocol and the cryptography needed to implement the main security objectives of the TLS Handshake protocol, namely entity authentication and key agreement. For the latter of these goals, public-key cryptography was needed, for the former, we used both public-key cryptography, especially digital signatures, and symmetric cryptography, especially message authentication codes (MACs).
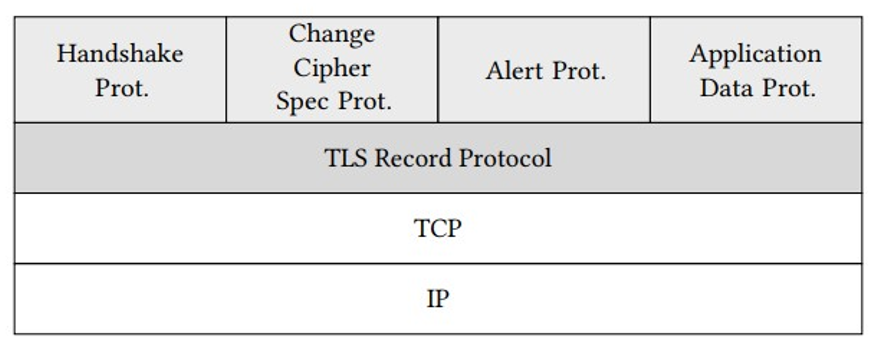
But entity authentication and key agreement are only prerequisites of the main goal of TLS, which is to establish a secure tunnel between client and server, providing confidentiality, integrity protection, and message authenticity. As already briefly discussed in Chapter 6, Transport Layer Security at a Glance, it is the task of the TLS Record protocol, located immediately above the transport layer (see Figure 14.1), to actually realize this tunnel. In order to do so, it takes a data fragment from a higher layer protocol, for example, HTTP or the TLS Handshake protocol, encrypts and authenticates it (if the necessary key material has already been agreed on), creates a record header containing the necessary information for the receiver to process the fragment, and puts the header and the protected data together to form a record. Finally, the protected record is transferred to the lower layer protocol.
In earlier TLS versions, the TLS Record protocol first computed a MAC over plaintext, then appended the MAC to the plaintext and finally encrypted the result. But this MAC-then-encrypt order of operation has turned out to be prone to attacks. We will cover some of these attacks in Chapter 21, Attacks on the TLS Record Protocol, in Part IV, Bleeding Hearts and Biting Poodles of the book. Today, special algorithms called authenticated ciphers, providing a more secure combination of encryption and authentication, are used in the TLS Record protocol. These algorithms are discussed in Chapter 15, Authenticated Encryption. Authenticated ciphers, in turn, use block ciphers, discussed in the present chapter, as their building blocks. Today, block ciphers remain the single most important cryptographic tool for providing confidentiality.
