TLS server state machine – TLS Handshake Protocol Revisited
13.2 TLS server state machine
The server state machine is shown in Figure 13.2. Like with the client state machine, labels in square brackets indicate actions that the server performs only under specific circumstances.
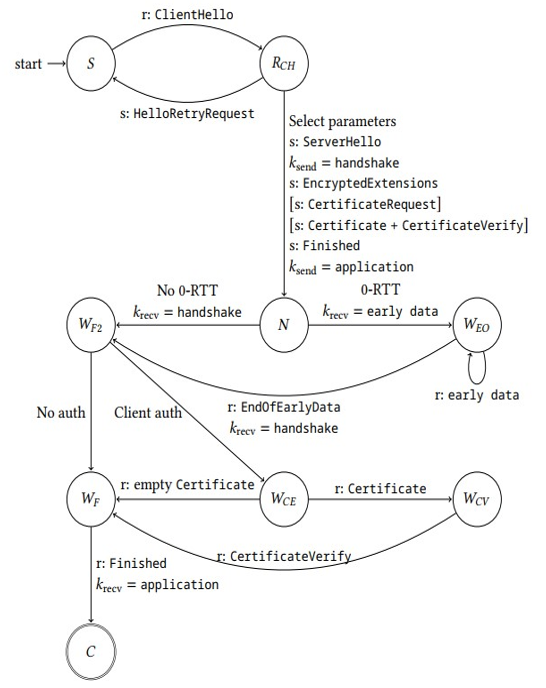
Figure 13.2: State machine and state transitions of a TLS 1.3 server
For server Alice, the TLS handshake is triggered by receiving the ClientHello message from client Bob. Upon receiving this message, Alice transitions to the state RECVD˙CH, denoted by RCH in Figure 13.2.
If Bob’s message contains parameters that Alice does not support, she replies with a HelloRetryRequest and switches into the initial state S.
Otherwise, Alice selects desired parameters from those offered by Bob in his ClientHello and replies with the ServerHello message. In addition, Alice sends EncryptedExtensions, encrypted with the handshake key.
Alice also sends the CertificateRequest message if she wants Bob to authenticate himself using his certificate. Moreover, if Bob has requested Alice to authenticate herself using her certificate, Alice replies with the Certificate and CertificateVerify messages. Alice then sends the Finished message and switches to the state NEGOTIATED, denoted by N.
If 0-RTT mode is desired, Alice uses the early data secret key and switches to the state WAIT˙EOED, denoted by WEO, where it receives early data from Bob. Upon receiving Bob’s message EndOfEarlyData, Alice transitions to the state WAIT˙FLIGHT2, denoted as WF2.
If 0-RTT mode is not desired, Alice simply sets the shared secret key for receiving data to the handshake key and switches to the state WF2.
If Alice does not want Bob to authenticate himself, she switches directly to the state WAIT˙FINISHED, denoted by WF . Otherwise, she transitions into the state WAIT˙CERT, denoted by WCE, where she waits for the Certificate message from Bob.
If Alice receives Bob’s Certificate while in state WCE, she switches to the state WAIT˙CV, denoted by WCV . Alice then waits for the CertificateVerify message from Bob and, upon receiving this message, switches to WF . Alternatively, if Alice receives an empty Certificate, she transitions directly to WF .
Finally, while in state WF , Alice sets the shared secret key to the application key and switches to the state CONNECTED, denoted by C.
